發(fā)布時(shí)間 :2021年08月07日
類型 :勒索軟件
近日����,亞信安全CERT 監(jiān)測(cè)到安全研究人員在blackhat安全大會(huì)上公開了 Microsoft Exchange Server 中的遠(yuǎn)程代碼執(zhí)行漏洞�����,包括漏洞細(xì)節(jié)���、驗(yàn)證視頻和部分PoC����,主要涉及以下三個(gè)漏洞:
CVE-2021-34473 :Pre-auth Path Confusion leads to ACL Bypass(ACL繞過漏洞)
CVE-2021-34523 - Elevation of Privilege on Exchange PowerShell Backend(權(quán)限提升漏洞)
CVE-2021-31207 - Post-auth Arbitrary-File-Write leads to RCE(授權(quán)任意文件寫入漏洞)
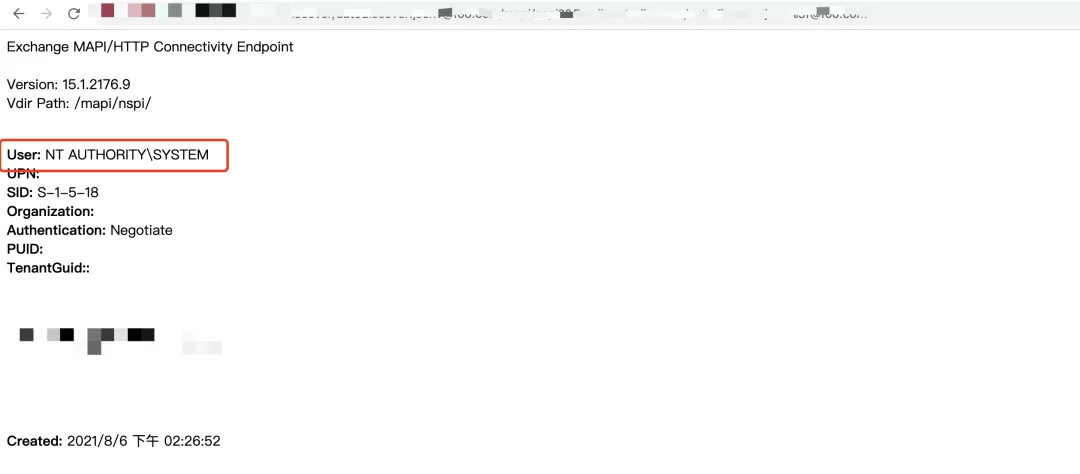
遠(yuǎn)程攻擊者在成功組合利用上述三個(gè)漏洞的情況下����,可不經(jīng)過任何身份驗(yàn)證在目標(biāo)機(jī)器上執(zhí)行任意代碼。鑒于這些漏洞的危害較大����,亞信安全CERT建議客戶及時(shí)修復(fù)相關(guān)漏洞��。以下為亞信安全CERT對(duì)CVE-2021-34473漏洞的復(fù)現(xiàn)截圖:
CVE-2021-34473 ����,CVSS評(píng)分為9.1CVE-2021-34523�����,CVSS評(píng)分為9.0CVE-2021-31207����,CVSS評(píng)分為6.6Microsoft Exchange Server 2010
Microsoft Exchange Server 2013Microsoft Exchange Server 2016Microsoft Exchange Server 2019官方已發(fā)布對(duì)上述利用鏈漏洞的補(bǔ)丁,請(qǐng)及時(shí)安裝相關(guān)補(bǔ)?����。?/span>
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207
https://i.blackhat.com/USA21/Wednesday-Handouts/us-21-ProxyLogon-Is-Just-The-Tip-Of-The-Iceberg-A-New-Attack-Surface-On-Microsoft-Exchange-Server.pdf
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207